![]()
By Ellen Nakashima March 26, 2018
Last week the U.S. government announced indictments and sanctions against an Iranian hacker network involved in one of the largest state-sponsored hacking campaigns the United States has ever prosecuted.
The nine Iranians named all were affiliated with the Mabna Institute, a private Iran-based company that the government alleges hacks on behalf of the Islamic Revolutionary Guard Corps and whose members sold the data for profit.
A private U.S. research company has been tracking the same campaign since late 2017, and on Monday released details that show the hackers targeted not just U.S. university professors, but also students and faculty to collect credentials for the victims’ university library accounts.
The Charleston, S.C.-based company, PhishLabs, earlier this year shared the data with the FBI. The firm called the campaign “Silent Librarian.”
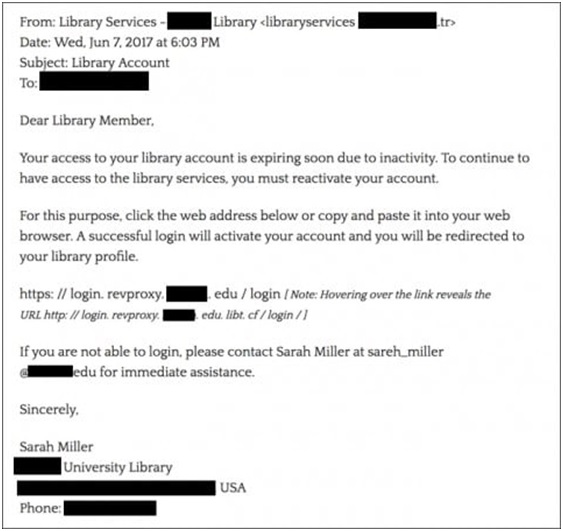 PhishLabs, a research company based in South Carolina, has tracked an alleged Iranian hacking campaign since last year and shared its findings with the FBI, including ”lures” like this email, which were used to steal log-in credentials. Crane Hassold, PhishLabs’ director of threat intelligence and a former FBI analyst, noted the email’s flawless spelling and grammar. (PhishLabs/PhishLabs)
PhishLabs, a research company based in South Carolina, has tracked an alleged Iranian hacking campaign since last year and shared its findings with the FBI, including ”lures” like this email, which were used to steal log-in credentials. Crane Hassold, PhishLabs’ director of threat intelligence and a former FBI analyst, noted the email’s flawless spelling and grammar. (PhishLabs/PhishLabs)
Starting with two domains that hosted nearly two dozen university phishing sites, the company analyzed Internet Protocol addresses and other open-source research to identify more than 750 phishing attacks attributed to the group.
A phishing attack involves a lure — usually an email — sent to a prospective victim and crafted to appear authentic, as if it came from a person or organization that the victim knows or could expect to hear from.
Most lures contain links that send the victim to a Web page designed to appear like a genuine company or organization (such as a bank, social media platform or an email log-in page). Once the victim enters his or her credentials, the hacker can access the person’s account.
In this case, PhishLabs collected several email lures that were used by the hackers to compromise university accounts. “The most notable thing about them was that they were incredibly realistic-looking,” said Crane Hassold, PhishLabs’ director of threat intelligence, and a former FBI analyst. “Their spelling and grammar was perfect. They were thematically relevant, naming the university in the lure.”
He noted that there were also some non-universities, such as Los Alamos National Lab, created in 1943 to design an atomic bomb and which is now one of the largest science and technology labs in the world.
The targets were not randomly selected, he said. “Most of the targets we observed were medical, research or technical universities, which are areas the Iranians are interested in.”
To date, he said, PhishLabs has identified attacks attributed to Silent Librarian dating back to September 2013. The hackers have targeted more than 300 universities in 22 countries. While most are located in the United States, Canada, Britain and Australia, schools also have been targeted in Western Europe and Asia, he said.
PhishLab also identified a website through which the Iranians were selling stolen credentials that was not named in the Justice Department indictment. The site, Uniaccount.Ir, is run by Mostafa Sadeghi, who is one of the Mabna Institute hackers named in the indictment.




